The Military's Losing War Against Data Leakage
Strava
The Defense Department can’t stop the rising river of of digital metadata — or prevent enemies from dipping into it.
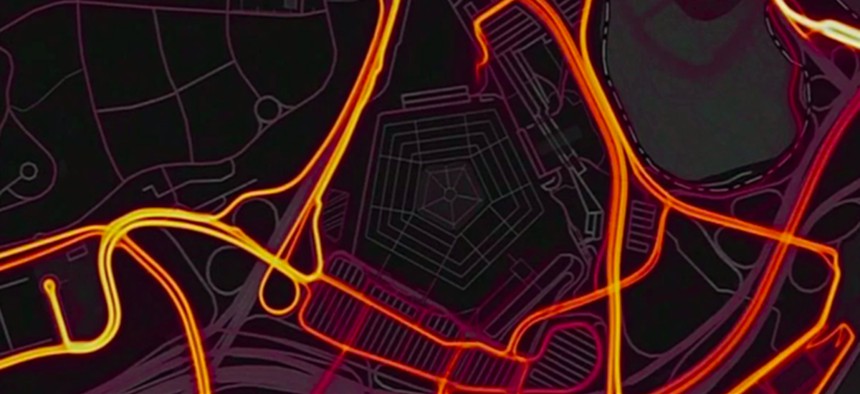
The Pentagon has long wrapped Diego Garcia in a veil of secrecy, barring media from the Indian Ocean island even as its base and airfield became a key node in America’s wars in the Middle East. But a hole appeared in the veil last Saturday, when a mobile fitness-tracking app company called Strava posted a heatmap of its subscribers’ activity — including the routes that sailors and airmen take as they jogged.
“What you saw from the running patterns is exactly what I experienced when I was deployed there five times between 1985 and 1999,” Air Force General Paul Selva, vice chairman of the Joint Chiefs of Staff, recalled in a breakfast with reporters on Tuesday. A heavily secluded jungle trail runs along the island’s western edge, Selva said, perfect for an ambush. “I’ve run it a thousand times. If I had a FitBit, I would have contributed to the map of Diego Garcia.”
When news of the heatmap and its potential effect on the military reached Defense Secretary James Mattis last weekend, he ordered an immediate review of Defense Department policies related to wearable electronics. Now Mattis is reportedly considering a ban on personal smartphones in the Pentagon.
“We currently have annual training for all DOD personnel” about social media and wearable device do’s and don’ts, Pentagon spokesman Col. Rob Manning told reporters Monday. “With emerging technology there is always a need to reinforce operational security and force protection…We are going to take a look at our policies” he said. When asked if the Strava map revealed information that was sensitive or secret, Manning offered an artful dodge. He was “not aware” that it had, he said. When asked if the policy review would be looking at smartphones and potential restrictions on them, Manning answered “absolutely.”
Ban or no ban, the military will have a hard time reducing the amount of digital metadata that may compromise the way it works, trains, and fights wars. That’s because the Strava heatmap phenomenon is not just an isolated operational security failure but an example of what hacker-author-astrophysicist Alasdair Allan has called data leakage. It’s a trend that’s directly linked to the expansion and interconnectedness of the digital universe, and one that the U.S. military has no chance of stopping.
Consider that the wearable device market is forecast to double by 2021, when 222.3 million units will be shipped annually, according to a forecast by research firm IDC. The U.S. military, both as an institution and as a collection of people who share a certain competitive nature, represents the ideal market for fitness apps and gear. Indeed, the military has itself spent more than $2 million on the very FitBit devices that last week caused it so much trouble.
But before the military began to worry about the biometric metadata that soldiers were creating, it was broadcasting its plans to collect and widely use it. For example, the Pentagon hopes such data can help it ditch the Common Access Card currently used to protect devices and installations.
“In the future, we see that the systems you carry on you, developing information on you and taking information from you,” Lt. Gen. Alan Lynn said last June. Lynn, set to retire shortly, leads the Defense Information Systems Agency — the U.S. military’s ITprovider. “Your walk is as individual as your thumbprint. Why is that important? Well, if you are in warfighting, oftentimes you wear gloves, oftentimes you wear masks…you can’t use a lot of the biometrics you would normally use. But your gait, your walk, that’s going to be there. We think [identity-based access and permissions are] an important part of our future for identity.”
“You go to your workplace; you go home; you notice your phone already registers those two places? Because it knows where you’re going. Those are patterns of life. Those are things that can be imported into the device,” as a means to verify identity, said Lynn. He offered that it was DISA’s goal to use those signals toward multi-factor authentication in the military.
Of course, collecting and transmitting biometric data need not be as insecure as it was in the Strava case, which was largely the result of users setting privacy preferences that allowed the app to use and publish the information. But the makers of such apps and services have vested interests in getting users to share as much data as possible: all companies scrutinize it to understand how people use their services; many also sell it to whomever will buy. Most of the data is supposed to be anonymous, or run through a process called anonymization that strips it of personal info. But anonymization is hardly a foolproof concept. Consider the work of MIT data scientists César A. Hidalgo and Yves-Alexandre de Montjoye who showed in 2012 that four location data points were enough to de-anonymize an individual.
This makes moving people around without revealing who they are a “very serious challenge” even for the CIA, according to Matthijs Broer, chief technology officer at the agency’s Directorate of Science & Technology.
Broer alluded to Hidalgo’s work at MIT at the Defense One Summit in November: “There have been some studies done in the open…where all I have to do, I don’t even need to know who you are…but with four measurements of your digital dust, and a modest amount of computational horsepower, I can completely nail who you are and where you are in the world at any time.”
Your identity reveals itself through the places you’ve been. In the era of ubiquitous smart devices, that’s not a poetic notion so much as a literal truth. But in order to reliably convey that data, that device needs to be in constant communication with an exponentially expanding menagerie of third parties, cellphone towers, apps, companies, etc.
But opting out of biometric data collection will become harder — and potentially even conspicuous. Many troops, of course, may simply be ordered to give up their biometric data as a condition of their service. But many banks, civilian workplaces, and even consumer electronics already use biometric technology for identity verification. By 2020, facial and other biometric identity indicators are expected to be a $24 billion market.
The military can try to keep a lid on all this data, but clever adversaries will always find ways to exploit data in our our ever-more-quantified world. Selva noted that you could, in theory, find top-secret U.S. satellites by watching hobbyists.
“Space is a really open architecture. If you have enough hobbyists with telescopes, you can detect all of the satellites in low earth orbit. If you know where all those hobbyists are, can precisely map their GPS coordinates, and you can map the time they saw the object that you’re interested in, you can develop a reasonable detection and targeting system without having elegant radar and telescopes yourself. Russia and China possess both elegant radar systems… and they’re able to subscribe to all of those capabilities that exist simply because they exist.”
It’s one reason why he wears a non-digital mechanical watch.
Data leakage is a fact of the exploding data universe. Still, there are ways to reduce its impact. The military could better control the specific apps it lets soldiers download (or mandate devices that show which apps do third-party data siphoning.) It could make more liberal use of data decoys or honeypots in areas of high sensitivity, including space. And it could refine how it detects events like the Strata heatmap and responds to them.
Asking the world to create less data is not a strategy. It’s a prayer that won’t be answered.
NEXT STORY: DHS Beats Government Privacy Average






