Congress Doesn’t Know How to Count the Number of National Security Professionals and That’s a Problem

Proposals by Congress to cut the number of security clearances doesn’t address the true problem. Blablo101/Getty Images
Instead of addressing data security or IT policies around protecting classified information, Congress goes after numbers.
Last week Congress pushed out two bills aimed at reforming the security clearance process, a topic that has been debated since classified documents were found at former president Donald Trump’s Mar-a-Lago residence and which reached fever pitch following the alleged breach of significant amounts of classified information by Massachusetts Air National Guardsman Jake Teixeira. The Classification Reform Act of 2023 and Sensible Classification Act of 2023 both propose a number of changes to the governance and accountability of the classification process, along with steps to reduce overclassification.
While much of the proposed policies will likely go unnoticed by most federal offices, the last section of the Sensible Classification Act of 2023 includes provisions that could have a significantly negative impact on the national security hiring space. The language echoes a common problem with understanding the security clearance process today and how agencies track their cleared personnel.
The Sensible Classification Act states the “sense of the Senate” that “the number of people with access to classified information is exceedingly high and must be justified or reduced.” It goes on to require agencies to give an account for their eligible cleared population, along with plans to reduce the number of individuals eligible for classified information.
The bill runs counter to current market reality and flies in the face of what has been one of the most significant federal government hiring pushes in decades, as many agencies look to onboard and attract new talent to take the place of a graying government workforce. The vast majority of those positions require some level of security clearance. And while government contracting cycles move 12 to 18 months into the future, the Sensible Classification Act calls for plans to reduce the cleared workforce within the year. The legislation asks any agencies with classified workers to provide an accounting of the number of individuals eligible for a security clearance within their agencies, along with plans to reduce that number.
The bill goes on to require, “a description of how the agency head will ensure that the number of security clearances granted by such agency will be kept to the minimum required for the conduct of agency functions, commensurate with the size, needs, and mission of the agency.
The legislation echoes the drumbeat of Congress over the past month. Sen. John Cornyn, R-Texas, called the number of individuals with security clearances “crazy.” Sen. Mark Warner, R-Va., argued in a press conference recently, that too many people have security clearances, and that led to the recent leaks and unauthorized disclosures.
It’s not the first time Congress has gone after the number of individuals who have a security clearance in order to combat breaches that were actually caused by lax security procedures. The number of individuals with access to classified information has generally been blamed for the problem of leaks. Current legislation rightly frames it as a consequence of overclassification, but rather than addressing data security or IT policies around protecting classified information, it goes after numbers.
A zero trust framework is good for IT, but unfortunately doesn’t work for people – where the reality is we’re always only in a position to reduce risk, not eliminate it. Proposals by Congress to cut the number of security clearances doesn’t address the true problem, which is how lax security procedures have allowed for the printing and removal of classified documents from cleared facilities – which has been the case for nearly every major leak scenario over the past several years.
Eligibility vs. Access – There’s a Difference
It’s easy to critique the number of individuals with a security clearance, where at face value, four million people with access to sensitive information appears like a lot. Breaking down the number further and considering what the term “eligible to access classified information” means is key to understanding why the number of individuals with classified information isn’t the problem.
In quarterly progress reports the government already tracks and provides information on its eligible vs. in-access cleared population. The number of individuals with access is always significantly lower than the eligible number. It includes active duty service members, federal government civilians, and government contractors.
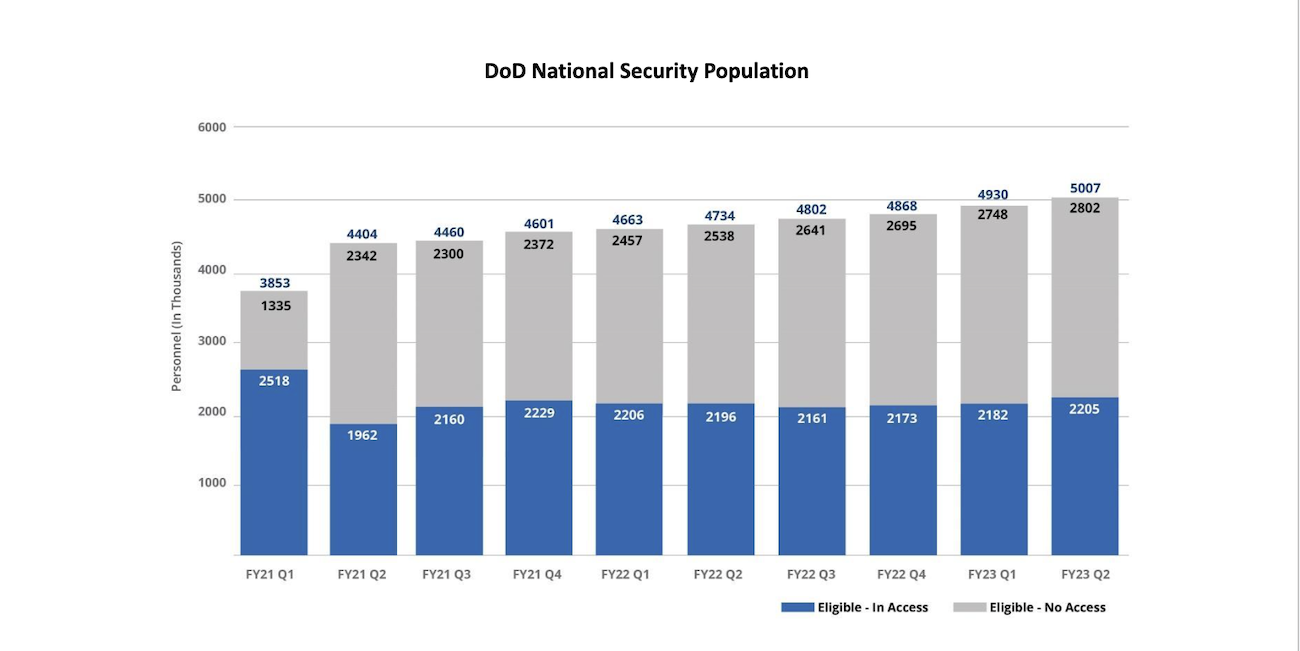
The Defense Department, specifically, saw a dramatic drawdown in the number of individuals with access to classified information following the pandemic – and today’s in-access population remains 300,000 individuals lower than it was prior to the pandemic. The blue bar indicates the number of individuals who are actually using their clearance eligibility within DOD today. Access is based on the position, and eligibility is tied to the person. If you’re eligible, but not in access, that means you’re not accessing classified information in your current position – but you remain eligible to do so, a supply-demand elasticity that is critical to ensuring employment mobility and allowing national security professionals to move across positions or organizations without requiring a new security clearance investigation. By drastically cutting eligibility, you also eliminate the government’s ability to scale up its workforce as needed. There is a cost component, as well. Reducing the number of individuals with clearance eligibility means you’ll need to process more new investigations – a process that is currently going up and takes an average of 137 days for a Top Secret security clearance for DoD/Industry applicants – and a cost of more than $5,000 per applicant.
It's the right thing to look at access and ensure only those who need it do. But cutting clearance numbers does nothing to improve security or eliminate risk. Desk audits of the cleared workforce have happened before – and did nothing to stop the Navy Yard shooter, Reality Winner, or Harold Martin.
The Senate’s current legislation considers the supply of security cleared talent while making no mention of current hiring needs or the national security implications of a graying workforce and reduced cleared talent pool. Today, the government needs more individuals willing to obtain a security clearance and support national security – not less. In January, the NSA announced one of its largest hiring surges in 30 years. Last month FBI Director Chris Wray emphasized there are 50 Chinese hackers to every one FBI cyber professional in his request for an additional $63 million to help the agency increase cyber capacity and hire 192 positions. Those jobs all require a security clearance.
The government does not have four million people with a security clearance today. It has roughly 2 million individuals with access to classified information. You can argue that even that figure is too high, but you shouldn’t eliminate it until you create hiring authorities, labor category reforms, and government office credentialing plans that indicate how you will keep your work and workforce safe, when you have uncleared professionals working in close proximity to our government’s secrets.
Cutting the cleared population signals that the Senate wants less vetting, and less security – at a time when it should be demanding greater protocols around protecting sensitive information. Security clearances provide eligibility – but they also create penalties for unauthorized disclosures. And they also come with punitive responses for those who break the government’s trust.
A blanket reduction in the size of the cleared workforce – which is the reality you’ll get when you tell your agencies they have too many cleared people – will affect the mobility, upskilling, and diversity of our national security workforce. Let the market and the threat landscape dictate the number of security clearances. Don’t let a negative news cycle do it.
NEXT STORY: DHS Unveils Departmentwide Body Camera Policy





