sponsor content What's this?
Why DISA Has Embraced SDN for the Pentagon

Presented by
FedTech

Software-defined networking makes it easier to provision networks for the Defense Department and also enhances network security.
The Defense Department has been called the largest bureaucracy in the world, so it would not seem natural for it to adopt more cutting-edge technology all the time. However, that is what it is doing when it comes to networking.
The Defense Information Systems Agency, the Pentagon’s IT services arm, has been busy adopting and deploying software-defined networking technology. DISA has turned to SDN to make it easier for DOD components and combatant commands to set up networks, deliver services and ensure that networks are secure.
Although network security was not the primary motivator for DISA’s deployment of SDN, it has been one of the welcome byproducts. DISA announced its shift to SDN in June 2017 via a contract with Leidos and AT&T, in which they agreed to engineer and deliver SDN controller technology into the Department of Defense Information Network.
Paul Inverso, the technical manager for Software Defined Enterprise at DISA, says the agency has progressed from piloting SDN initiatives to the deployment of full-scale production services based on software-defined technologies.
The initial pilot provided rapid provisioning services for Layer 2 and Layer 3 virtual private networks for a portion the DISA IP network, he says. The pilot reduced service provisioning time by up to 45 days, Inverso says.
“Based on its success, the pilot is extending to the full IP network of more than 500 nodes,” he says. “DISA is also upgrading the compute and communication infrastructure in all of its data centers with SDN technology. Initial deployments include SDN controllers providing automated control over network elements, while the orchestration function will be implemented in a later phase.”
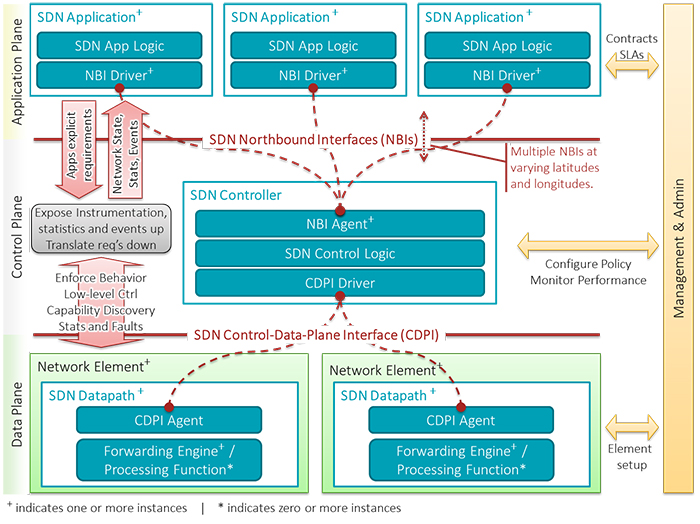
What Is SDN?
Let’s start by understanding what SDN actually is. SDN decouples the network control plane from the data plane, enabling abstraction of resources and programmable control of network resources.
Thus, SDN makes networks “more open and interoperable, leading to lower costs, increased flexibility and control, plus greater innovation,” a CDW white paper notes.
Instead of linking network functions and policies to hardware, SDN enables agencies like DISA to control those tasks through software. As a result, these technologies can streamline management costs for complex networks and can significantly shrink the time it takes to deliver network resources.
“SDN’s open and programmable application programming interfaces (APIs) for policy-based management and security allow organizations to automate formerly tedious and time-consuming manual configurations, reducing the workloads of IT team members,” the CDW white paper notes. “Rather than requiring an IT staff member to manually configure each hardware component, SDN allows data centers to roll out network configurations and updates simply by sending out software updates.”
Network intelligence is “logically centralized in an SDN controller software that maintains a global view of the network, which appears to applications and SDN network policy engines as a single, logical switch,” sdxCentral notes.
Why DISA Chose to Deploy SDN
Robert Kimball, technical adviser in the Cyber Directorate at DISA, says that the agency has adopted “a much more expansive approach to software-defined technologies beyond SDN.”
The Software Defined Enterprise at DISA “aims to introduce automation into every DISA program where it will improve service to the warfighter and our mission partners.”
The primary motivation for doing so is to reduce the time it takes to deliver services, whether in the WAN or data center, Kimball says. “DISA will also realize efficiencies, which will allow us to tackle more complex issues by reducing manual processes,” he adds.
Inverso says the DISA SDE architecture is built from a hierarchical structure of orchestrators and controllers. “Orchestrators interact with business systems, mission partner requirements, and the operational state of the network to direct automation,” he says. “The controllers will be network-specific and will implement the direction of the orchestrators and interface with the network equipment.”
SDN Security: The Cybersecurity Advantages of SDN
SDN enables network administrators to have a high-level view of the entire network and quickly modify rules to enhance security, TechTarget notes. SDN also enables faster traffic shaping techniques. Perhaps most importantly, SDN enables admins to limit the outbreak of malicious activity across the network from a centralized control plane.
Lt. Gen. Alan Lynn, DISA’s former director, said in November 2017 that by virtualizing networks and replicating them in the cloud, the DOD makes its network infrastructure more secure.
“It’s easier to defend a network if you can build multiple, equal networks that are identical in a row,” Lynn said, according to FedScoop. “And then if you have an attack on one of the networks, you can fold that network and move your users over to the next network.”
SDN will allow the Pentagon to switch between identical virtual networks constantly, similar to how modern radios can switch to the best frequency all the time. “You can’t have a persistent attack if the network isn’t persistent, if it’s constantly moving,” he said.
Inverso says that initial deployments of SDE present the DOD with a different security environment than it faces right now. “The concentration of network control into a set of automated tools changes the threat landscape and requires additional protections than are used on traditional networks,” he explains.
This concentration of network command and control into “a more defensible enclave” is one of the benefits of SDN, he says. “This enclave can be protected at the same level as national security information, protections that are not possible in traditional networks with distributed command and control,” Inverso says. “By having an SDN controller deploy tested/validated configurations to the network, we increase the network efficiency and simplify the management of the network.”

Kimball says that the current deployment is a “prelude to the ultimate security benefits of SDE.” Adversaries are already starting to explore attack techniques using machine learning and artificial intelligence, Kimball notes. The only way the Pentagon can keep pace with the cybersecurity arms race is to “provide defenses operating on the same time scales.” Integrating SDE technologies with defensive cyberspace operations tools will “provide network defenders the ability to prevent disruption by the most sophisticated adversaries,” Kimball says.
Kimball notes that security “was not the motivating factor for deploying SDE,” and that “reducing service delivery intervals and improving efficiencies were the primary drivers.”
Indeed, he says that the security challenges, at least initially, “certainly outweighed any security benefits.” However, Kimball adds, “the work required to deploy an SDE-enabled network provides a much more secure network than is possible with traditional network technologies.”
The paradigm shift in the DOD toward providing data protection, rather than network protection, “is not possible without wide-scale adoption of SDE technology,” according to Kimball. Finally, he says, “the fact that sophisticated adversaries were adopting advanced technologies countered only with SDE technology was a factor in pushing SDE technology past the pilot stage into full production.”
The Importance of SDN Controller Security
Although SDN brings many benefits in terms of network security, it does have its weaknesses.
“A significant issue regarding SDN security is that virtualizing every aspect of the network infrastructure increases your attack footprint,” Network World reports. “The SDN controller is typically the primary target for attackers because it is the central point for decisions in a network and a central point of failure.”
Scott Hazdra, principal security consultant for Neohapsis, a security advisory company that is now part of Cisco Systems, notes that the SDN controller must be a key priority when it comes to security.
“Because the control plane plays a critical role and changes are typically propagated throughout the network, ensuring that applications are authenticated, connections are securely encrypted, security policies are properly applied and that there’s a system for creating audit trails is essential,” he told Network Computing. “It’s also very important to control who has access to the control plane and maintain strict change control procedures.”
At DISA, Inverso notes that, as with all systems DISA deploys, the SDE orchestrators and controllers “are evaluated in accordance with a cyber-risk framework.”
The exposure to external data, criticality of function and other factors dictate the actual set of protections for each controller and orchestrator, he says. DISA published an “SDN Controller Security Requirements Guide” which provides network administrators the baseline checklist to secure the device.
How SDN Deployments Will Move Forward
The initial SDE deployments within DOD “are concentrated on areas showing immediate benefits from automation, such as network provisioning, and rolled out on a program-by-program basis based on criteria examining improved service delivery or enhanced automation capabilities,” Kimball says.
Other high-priority programs are those with requirements that can be satisfied with SDE, Kimball says, “but are out of reach of traditional network technologies.”
DISA is committed to an open multivendor SDE environment, Kimball notes. DISA expects to field a number of different SDE controllers that meet the unique requirements of individual programs, he adds, and the agency will begin the acquisition process for a global orchestrator in fiscal year 2019, which starts on Oct. 1.
“DISA will also deploy service-level orchestrators that are specific to major parts of the enterprise, like WAN transport or data centers,” Kimball adds. “Once the SDN efforts achieve sufficient maturity,DISA will migrate our cyber defenses to SDE and take advantage of machine speed response to cyberthreats and active cyber defense.”
How might DISA’s adoption of SDN impact other federal agencies? SDN is one of the key elements that agencies will likely deploy as they modernize their networks and IT infrastructure as part of the General Services Administration’s $50 billion Enterprise Infrastructure Solutions contract.
Steve Wallace, technical director of DISA’s Development and Business Center, says that “all risk assessments are local, and agencies must evaluate their individual risk frameworks and whether lessons learned from DOD applications are applicable to their respective situations.”
Wallace notes though that “DISA partners closely with other federal agencies to advance overall understanding of the security benefits of SDE.”
“As one of the most forward-leaning agencies in the adoption of SDE technology, DISA is committed to collaborating with all federal agencies with interests in this area,” he says.
This content is made possible by FedTech. The editorial staff of Nextgov was not involved in its preparation.





