How to catch the attacker with valid user credentials
Behavioral analysis could make continuous diagnostics and mitigation more effective than ever.

Mark Seward, VP of marketing at Exabeam.
It’s time to admit that we’re losing the cyberwar.
Hacker groups are highly organized and mobilized, and they are increasingly using sophisticated attack techniques and tools to defeat longstanding cybersecurity defenses. Data breaches at major enterprises have become a common occurrence, and well-funded nation states are taking a major interest in cyber espionage activities.
In response, the federal government launched a $6 billion continuous diagnostics and mitigation (CDM) initiative two years ago, led by the Department of Homeland Security (DHS) and the Office of Management and Budget (OMB), to provide federal departments and agencies with goals of strengthening cybersecurity defenses to combat today’s cyberattacks through continuous monitoring of agency risk posture. Broken into four implementation phases and 15 capabilities, this cross-agency cybersecurity initiative is the largest the federal government has undertaken in the past decade.
To mitigate the threats of today’s hackers, agency IT security teams need to continuously focus on where the attack surface exists today -- not only at the network perimeter, but within the network itself. In 2012, Mandiant’s M-Trends report showed that attackers used valid employee credentials in 100 percent of targeted attacks. This tactic allows hackers to impersonate legitimate users throughout the IT environment.
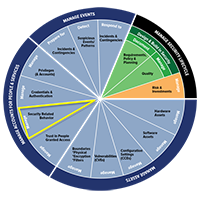
In CDM's implementation phase two, which is called “managing accounts for people and services,” there is a capability most agencies organizations don’t fully grasp: security related behavior. (See Figure 1)
In describing this capability, DHS provides examples that link the security training of employees to their use of credentialed access. However, employee training alone isn’t effective for preventing social engineering attacks, as it takes only one employee opening the wrong attachment to compromise a network and cause a data breach. IT security teams must be able to tell the difference between the way normal users use their credentials and the way an attacker would use those same credentials to achieve their objectives. It is through this sort of user behavior intelligence that an entire attack chain can be exposed.
One of the biggest challenges in today’s cybersecurity climate is security noise pollution, and the difficulty of knowing what’s anomalous in an ocean of normal user activity data. Security information and event management (SIEM) deployments were supposed to give IT security teams the insight they needed to address imminent threats. However, the thousands of unprioritized SIEM alerts generated per day drown out valid indicators. Also, it’s unlikely that an attacker with valid user credentials would ever generate an alert from any part of the traditional security infrastructure.
User behavior intelligence solutions, a relatively new solution category, autonomously and continuously ask questions about the characteristics of access and follow the use of credentials through any kind of account by switching across a session of activities from log-on to log-off -- all while comparing these activities to those of their peer group. In this manner, machine-learning technologies separate normal user behaviors from those of an attack. Credentialed activities are given an additive risk score based on each characteristic and fact gathered by the system during the session to quantify risk and seriousness of the threat. It’s the equivalent of having on the team a data scientist who can remember and track hundreds of thousands of users in real time, all while using current SIEM and log management repositories. Not only that, user behavior intelligence can also highlight the gaps in employee security awareness training that need to be rectified.
The recent spate of large data breaches indicates that strengthening perimeter security is only one part of an overall cybersecurity strategy, as most attackers have found that human employees are the easiest weaknesses to exploit. Employee training, while certainly important, does not negate the proclivity of errors in human judgment. To win the cyberwar, federal agencies need to realize what attackers value most – valid credentials – and use it against them.