The Hidden History of Encryption

andrey_l/Shutterstock.com
The technology that keeps your text messages private had its start on the banks of the Tigris River, 3500 years ago.
Never in history have more people had access to advanced encryption in their homes, offices, and pockets. The most basic online transactions and communications that Internet users conduct every day are thoroughly encrypted in transit, and are undecipherable without proper keys.
The democratization of encryption is a recent phenomenon: Only since the 1990s has computer encryption been open and freely available. But humans have been communicating with codes and ciphers for thousands of years, using rudimentary encryption methods to protect trade secrets and military orders, or simply to keep information private from neighbors.
For Gerhard Strasser, the story begins more than 3000 years ago, in Mesopotamia. Strasser, who studied the history of cryptology for decades at Pennsylvania State University, traces the development of encryption through the Middle East and Europe, and even to India, where it's mentioned in the Kama Sutra. He tells of a Medieval German cryptographer accused of black magic, and an 18th-century government minister in France who devised an ingenious way to spy on visitors.
I spoke to Strasser, now a professor emeritus in his native Germany, about the deep history of encryption. A transcript of our conversation appears below, edited for concision and clarity.
Kaveh Waddell: What’s the earliest example of humans encrypting their everyday language to keep it secret from others?
Gerhard Strasser: There is one very well written-up and documented cuneiform tablet in Mesopotamia, found around 1500 B.C. It was an encrypted message in which craftsmen camouflaged the recipe for a pottery glaze that was a highly coveted item at the time. As it turns out, later on, the secret had been unearthed and discovered, so later recipes were no longer encrypted because just about everyone knew it.
That was an interesting detail from a city along the banks of the Tigris River around 1500 B.C. So very early on, there certainly were commercial interests in cryptographic communication, as much as there may well have been military interests.
Waddell: Do we know how that message, the recipe, was encrypted?
Strasser: It was encrypted through a relatively simple substitution method: One cuneiform symbol was used for another. That way, basically, the message got garbled. But it was good enough for any layman—anyone not initiated—not to decipher it.
Waddell: This is a very early example. Is it isolated, or do we keep seeing basic forms of encryption in the centuries that follow?
Strasser: It was relatively isolated, quite frankly. It’s very early, obviously preceding Roman and Greek examples. You probably have heard of the atbash system, which certainly predates the birth of Christ. Again, a simple replacement of the last letter in the alphabet with the first letter, the second-to-last with the second—a simple transposition of letters which was good enough, and was used in the Bible.
So we have Hebrew ciphers. We also have—and this I found surprising—a mention, and a rather serious one, in the Kama Sutra, in India, from about the 4th century. We actually have a reference in the 44th and 45th chapters that men and women should practice cryptography.
Waddell: That’s not what one usually imagines is in the Kama Sutra. Why is this book talking about cryptography?
Strasser: Well, the Kama Sutra deals with, primarily, all sorts of—shall we be neutral?—intercommunication between men and women. Such communication obviously could entail secret communication. It’s that communication where men and women should have a language of their own, so that the neighbors could not understand.
Waddell: It sounds like different forms of cryptology developed early on in separate parts of the world. Were different techniques developed separately—did they crop up on their own—or was there a sharing of techniques?
Strasser: The sharing of techniques came later. Early cryptology began with the spread of a new religion and the Arab conquest, for five major reasons. Very early on, the Arab World had to rely on translations; it also had to study its own language. There were well-known advances in mathematics. There was a need for effective administration in the Arab Muslim state, a realm that kept on spreading. And ultimately, there was the very early diffusion of reading and writing.
It is absolutely fascinating how in the 800s, early on, such fundamental tenets like statistical techniques were developed, which took the West centuries to develop. When frequency analysis was discovered in the West, [Mesopotamian mathematician and philosopher] al-Kindi had already done it, in the 850s or 860s. He comes up with substitution ciphers, he comes up with transposition ciphers, developments that in the West begin around 1450 or so.
Waddell: Why does it take so long for Europe to develop these techniques that had been around for so long in the Arab world?
Strasser: Necessity is the mother of invention. The real necessity for such a development of cryptological means begins with diplomatic communication and rivalry between states. [In Europe], it begins rather locally in Italy. There is a plethora of city-states, and communication between these individual units needed to develop along certain secret lines. So maybe in the 13th, 14th centuries, Italian city-states and the Vatican began developing their own systems, simply because their reliance on plain messages didn’t work anymore.
Ultimately, this led to the official need for such a system for the papal court, and that is where the Italian Leon Battista Alberti comes in. Alberti was asked to develop a system, and he does so around 1450, when he comes up with a famous cipher disk, which is a spectacular invention, and clearly does not come from Arabic sources. There are some indications that some of the Arabic knowledge had reached Italy by that time, but there is no indication that such a cipher disk had been developed in Arab countries.
This is certainly the first very, very important invention in Western cryptography.
Waddell: So by the time we were just talking about, in the Arab World and in Europe, is cryptology still accessible to common people, or is it only used by elites and those in power?
Strasser: Some monasteries also used simple substitution systems. I’ve come across manuscripts, very serious religious manuscripts, where the poor scribe—who was bored stiff, obviously—started putting cryptographic systems right in the margins, and never erased it later on. They would even send each other such messages within the monastery.
Waddell: You’ve studied some early cryptographers whose work was compared to magic—and in one case, a cryptographer who was accused of wielding “black magic.”
Strasser: Yes, the poor Trithemius was his own worst enemy. He devised a spectacular cryptographic system in his Steganographia, and before he’d even finished it—he never finished it—he informed a fellow monk of what he was going to do, and that fellow monk totally misinterpreted the letter and accused him of black magic, which got him into a lot of trouble. The Steganographia wasn’t published until 110 or so years later.
It isn’t surprising that Trithemius was accused of black magic, because nobody could make heads or tails of the book.
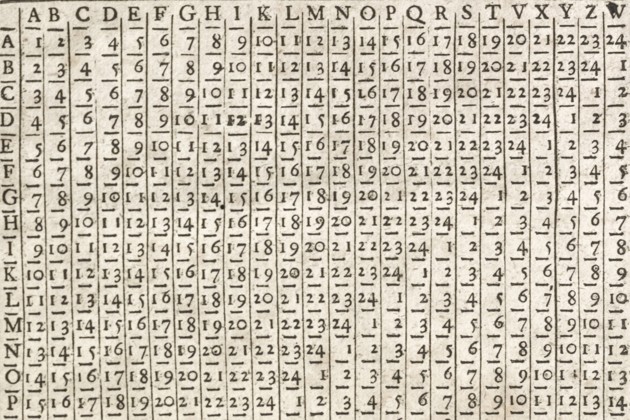
Waddell: What other technologies and techniques do you think were particularly novel or ahead of their time?
Strasser: The cipher disk was certainly ahead of its time. No doubt about it.
Later, Trithemius, in his second and immediately published book, Polygraphia,presents a 24-letter square. The square does the same thing that the cipher disk accomplishes— however, it has one very nice advantage.
A soldier in the field has a hard time cutting out two concentric paper disks and labeling them, while it is so easy for anyone to write 24 letters, write them horizontally and vertically, and shift them by one letter each line. That is a very practical application that Trithemius did not foresee. But it was so much easier for someone in the field to write his own square, and have a powerful cryptographic tool.
Waddell: Generally, it seems governments were ahead of the curve, and are essentially able to surveil communications through institutions that open them up, read them, and send them along their way.
Strasser: There’s no question about that. But we should not underestimate commerce. The Duke of Wolfenbüttel’s son gives us a wonderful example of camouflaging an encrypted message by simply listing the pounds and tons of wheat that a merchant might ship from point A to point B.
In other words, it says, “I herewith send you an invoice for 17 pounds of barley and 22 pounds of wheat,” or whatever it was. Of course, the numbers are the encrypted message, which means your partner has to be able to decode these numbers, which means they both have to have a codebook. It’s as simple as that. Number 17 means “The Duke of Windsor,” if you will, and number 22 means “the Queen of England.” Merchants, indeed, used simple cryptographic systems to negotiate with their peers.
Waddell: You’ve written about the system developed by the Count of Vergennes in 18th-century France to work coded messages into, essentially, travel visas. Can you describe how that system worked?
Strasser: That system is absolutely mean. I have never come across anything like it. I presented it at an NSA conference, and people were flabbergasted.

[During the 18th Century], the Count of Vergennes, the French foreign minister, informed all his consular officials abroad that anyone applying for, you might say, a passport—basically, that’s what it was—had to submit himself or herself to public scrutiny, and was investigated. They either volunteered information, innocently enough, or employees in the embassy would go around and collect information on that person.
The person was analyzed as to physical features, like: Is he bald? Is he cross-eyed? Is he tall? Is he short? Does he have a pot-belly? Those are outward and simple features that any official could jot down when the person presented himself. But then, beyond that, there was: Is he married? Is he a good lover? Does he have a mistress? Not exactly “Does he have AIDS?” but just about. And what is his purpose for applying for a passport? To visit relatives? He wants to meet craftsmen, he wants to engage in commerce in Paris?
But then beyond that, the embassy official had to pass judgment on his psyche. Is he depressed? Is he an alcoholic? Does he look like an alcoholic? Is he friendly, is he outgoing? And all of that would they be translated into what you could call a relatively large calling card with his name, asking to see the Count of Vergennes.
And that calling card was embellished with a beautiful frame, and the frame carried a code. If it had a sunflower, it meant the man was friendly, and if it had a moon instead of the sunflower, then he was an aggressive type. When it carried 12 little circles, he was very wealthy. When it only carried 4 circles, then he was of average means. When it didn’t carry a single circle, he was poor. And so on.

Initially—and this was a problem—each of these embassy offices had to have an engraver who would personalize this card. When Vergennes realized that you had to have a whole legion of engravers sworn to secrecy, his next step was to have his own little printing press, and print this information, but now in numerical form. You now had, simply, lots of numbers, and they all had their meaning.
It started out in the upper-left corner with an N. If the N was tall, the man was tall; if the n was small, the man was short. If it had a circle behind it, it means he was married. And then came the numbers. So, of course, the person who had this card thought, “Aha, I am number 17,222.” In actuality, of course, this was all encoded.
And the irony was that this card was given to the traveler. It wasn’t given to him in a sealed envelope, no. He could see it and it was supposedly perfectly innocent. He was then to go to Paris and present himself to the Count of Vergennes, and the Count of Vergennes would probably spend two minutes with him, but would immediately turn around and either analyze the card or have someone on his staff analyze it, and if necessary, send a policeman after him, depending on the type of business or information that was available.
If you had a wealthy merchant—it would be indicated that way—then they would actually try to delay his return to his home country, by hook and by crook, because the longer such a wealthy person would stay in Paris, the more money he would spend. If the gentleman had a police record back home, then that was an indication to really keep an eye on him.
Waddell: Was that a particularly advanced system? The fact that the messenger was also the target, was that something new?
Strasser: It was, absolutely. You don’t normally entrust the messenger with the message. To carry your own death warrant is known in poetry or in drama—it makes a good read—but the system was actually so refined that after the French Revolution, it continued to be used into the 19th Century.
Waddell: At its essence, that’s the same idea that’s still used in modern cryptography: When an electronic message is encrypted end-to-end, the messenger has no idea what the message says.
Strasser: I would agree. But you have cryptology and you have steganography, meaning [a system where] you cannot detect a message. If I send you an encrypted message, if you can’t decipher it, you can tear it up. But steganographic communication means, at face value, visually, it looks perfectly innocent. Nonetheless, embedded in it, is a secret message.
Waddell: It’s probably safe to say that in no point in history have more people had access to encryption. You have a computer, you have a smartphone, you have a way to keep things secret. Is this unique, that in today’s world so many people have access to encryption that is too complex for most to understand?
Strasser: More than in the 19th century and the early 20th century, where a well-trained normal soldier could still be entrusted with encryption, this is now out of individuals’ hands.
You can go into the Internet and freely download encryption systems, some of them extremely powerful and perfectly adequate for communication between the two of us. That doesn’t necessarily mean that I would understand the system. But I can use it: Some programmer has prepared it for me, and for free.
A normal, able-bodied citizen who wants to keep communication between him and his lover, or whatever it is, secret—he will use the system, without understanding it.
(Image via andrey_l/Shutterstock.com)
NEXT STORY: IARPA taps Dixon as deputy director






