Inspector: Security Holes Found in IRS Obamacare System
A core IRS system for calculating Obamacare fees for health insurers and drug manufacturer has security weaknesses
A core Internal Revenue Service system for calculating Obamacare fees for health insurers and drug manufacturer has security weaknesses, according to an internal audit.
Under the Affordable Care Act, insurers must report their net premiums to the tax agency annually, and pharmaceutical companies must submit sales data from certain government programs.
The Treasury Inspector General for Tax Administration recently examined a new computer application, called the ACA Information Returns system and known as AIR, that processes these returns. The IG's heavily redacted 44-page report, released Tuesday, suggests, specifically, the agency neglected to check source code for bugs and fix security vulnerabilities.
"These security control weaknesses could impact the AIR system’s ability to reliably process the electronic form reports and to accurately determine the applicable fees," TIGTA Deputy IG for Audit Michael E. McKenney said in the report.
The AIR system began playing a key role in Obamacare in March.
The agency has "provided details on how to address 23 of the 25 critical and major failures and errors" identified by an IBM Guardium vulnerability assessment tool, McKenney said. The two remaining weaknesses are redacted. Of the problems discovered, 14 are not expected to be resolved until fall 2015.
All the security vulnerabilities detected were stricken from the report. The number of failures and errors documented during testing also are blacked out, both in the text and accompanying charts.
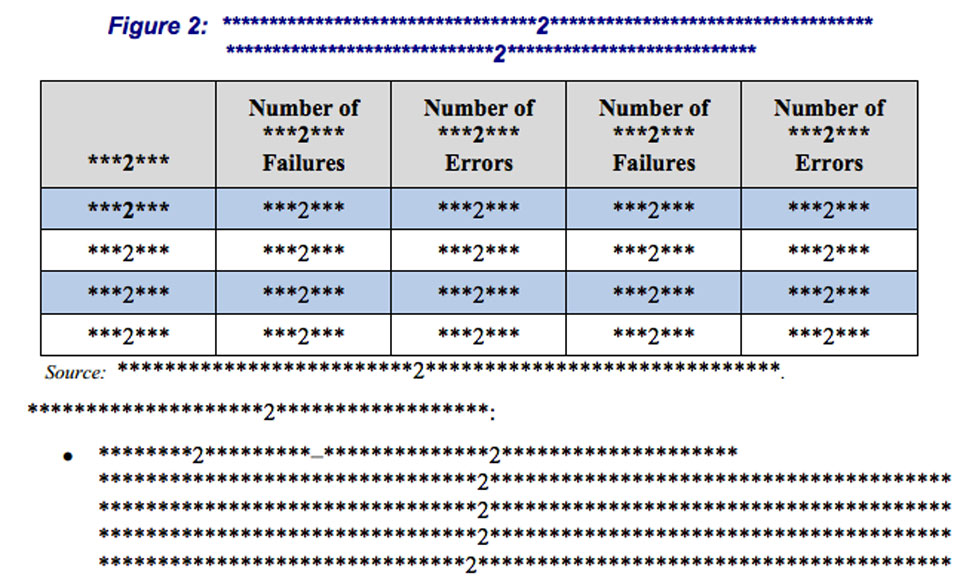
The IRS disagreed with an IG recommendation related to vetting code that runs an application for processing the industry returns.
The inspector’s advice and the IRS's reciprocating comments are largely redacted. But the inspector’s response to the agency’s objections suggests the IRS was not scanning code for security holes: "Source code scans are critical to help assess and protect enterprise software and applications from security vulnerabilities. Without a source code scan, security vulnerabilities may go undetected."
The audit was conducted from November 2013 through May 2014.
The computer applications probed are not part of the online insurance marketplaces, or exchanges, consumers use to sign up for Obamacare plans.
The Internet gateway into the exchanges, Healthcare.gov, has had its own share of security foibles. The Government Accountability Office in September cited inadequate security testing and noted the Centers for Medicare and Medicaid Services failed to apply software patches and did not properly configure an administrative network or require the use of strong passwords.
GAO’s findings came out a few weeks after CMS confirmed hackers had installed malware on a HealthCare.gov server. By November, CMS reported security gaps had been plugged.
Responding to a draft report, IRS officials in a Sept. 25 letter said the inspector’s recommendations “will contribute to our shared objective of identifying and mitigating security vulnerabilities.”
On Tuesday evening, IRS officials said in a statement the agency "has taken aggressive steps to ensure the protection of federal tax data" needed for complying with the Affordable Care Act. There have not been any system breaches involving information sharing, officials stressed. They declined to comment on the security holes cited and the source code issues.






