Malware
FY2025 NDAA targets spyware threats to U.S. diplomats, military devices
The language comes as the State department has pressed foreign governments to collectively set standards to prevent spyware abuses.
5 Russian military hackers plotted to spread malware to Ukraine through a US company, new charges say
The hackers also tried to target a federal agency based in Maryland, the Justice Department alleges.
US targets 6 to 8 month timeframe for new nations to join spyware pact
Six new countries joined the agreement last week, and the State Department was working behind the scenes to initially get more signed on.
Threat actor targeted DOD contracting website
Malware leveraging flaws in edge routers has been spying on military contracting websites, according to research from Lumen's Black Lotus Labs.
Report reveals 'sudden surge' in cyberattacks targeting government agencies
Cyberattacks impacting government agencies and the public sector spiked by 40% in recent months, according to a new report.
Top Malware of 2021 Has Been in Use for Years, CISA Warns
The advisory highlights that such usage offers “opportunities to better prepare” and provides recommendations to mitigate cybersecurity threats.
Taking Control of Ransomware and Other Malware with a Zero-Trust Strategy
Antivirus, sandboxing and similar detection techniques can’t keep up. It’s time for agencies to transform their approach to thwarting malware.
Facebook Can Sue Israel’s NSO Group, Appeals Court Says
The case against the NSO Group appears to scratch the surface of problematic commercial hacking tools sold at arms markets, which the U.S. government has only just begun trying to control.
U.S. Blacklists NSO Group and 3 Others for Selling Spyware, Hacking Tools
The Commerce Department says the companies—three from allied nations—acted against U.S. national security interests.
Report: Hackers Shift from Malware to Credential Hijacking
Cybersecurity firm CrowdStrike tracked record levels of cyber intrusion activity over the past year.
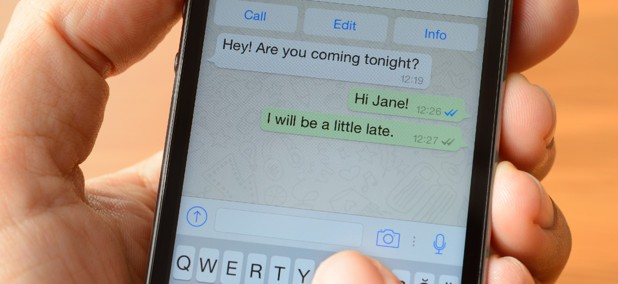
What Is Pegasus? A Cybersecurity Expert Explains How the Spyware Invades Phones and What It Does When It Gets In
Since 2019, Pegasus users have been able to install the software on smartphones with a missed call on WhatsApp.
National Lab Creates Technology to Detect Cryptocurrency Mining Malware
High performance computing systems are increasingly at risk.
Featured eBooks