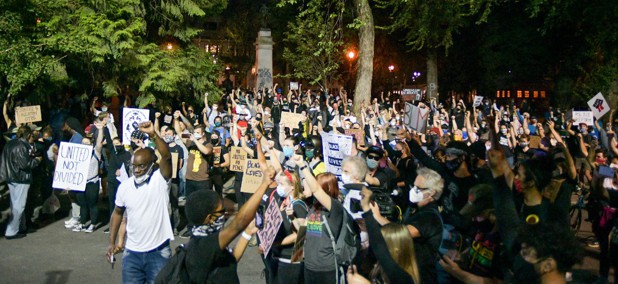Cybersecurity
CISA Leader Puts Health Sector Project on the Level of Election Security Initiative
A senior adviser brought in to boost the pandemic-driven effort says new materials are coming and stresses the importance of organizations acting on the agency’s advisories as part of their risk calculus.
Cybersecurity
CISA Reveals Timeline for Improving Anemic Information Sharing Program
The private sector has been pushing for greater liability protections before participating in a two-way exchange of cyber threats and vulnerabilities with the agency.
Cybersecurity
DHS Exempts Expanded Insider Threat Program From Key Privacy Act Provisions
The agency will be allowed to collect large amounts of data without having to follow several provisions regarding disclosure, relevance and the sharing of that information.
Cybersecurity
CISA Releases Tips For Secure Teleworking
The short guide offers quick tips and links to deeper resources for employees at every level.
Cybersecurity
Industry Groups Spar Over NDAA Provisions on Sourcing of Electronics from China
Dueling letters to lawmakers support and oppose language requiring the department to phase out the procurement of some basic technology from adversarial nations.
Ideas
It’s Time for Government Agencies to Secure Their Multicloud Environments
Multicloud environments can be extremely challenging to organize, manage and secure.
Cybersecurity
Post-election shutdown risk looms
Five weeks separate the November elections and the expiration date on the current stopgap funding measure keeping the federal government operational – and a path to avoiding a shutdown is not entirely clear.
Artificial Intelligence
House Passes Bills to Boost Emerging Tech and Shore Up Cybersecurity of Electric Sector
Lawmakers are calling for significant research and development efforts.
Cybersecurity
FCC Advances Order on Interagency Security Reviews of Foreign Applications
The effort tries to strike a balance between the desire to capitalize on foreign investments and managing threats from adversaries like China.
Digital Government
Federal Government to Conclude Fiscal 2020 With Record Spending
Even without data from the month of September, the Treasury Department reports total federal spending exceeded $6 trillion for the first time.
Cybersecurity
Foreign Hackers Cripple Texas County’s Email System, Raising Election Security Concerns
The malware attack, which sent fake email replies to voters and businesses, spotlights an overlooked vulnerability in counties that don’t follow best practices for computer security.
Cybersecurity
Industry Groups Ask Lawmakers to Remove Core Cybersecurity Provisions from NDAA
The trade associations for various government contractors are also opposing a range of oversight proposals in the annual defense bill, including ones aimed at enhancing procurement value and reducing unfair labor practices.
Cybersecurity
DOD releases interim cybersecurity rule
The rule is designed to ensure DOD contractors are adhering to a uniform standard for protecting controlled unclassified information is protected. But while trade groups representing government and defense contractors have lauded the framework but criticized the implementation and rulemaking process.
Ideas
Women Equal Men in Computing Skill, but Are Less Confident
Women in STEM careers remains around 24% even though women make up almost 50% of the overall workforce.
Cybersecurity
Defense Department Certification Body Could Itself Conduct Audits Under Interim Rule
One lawyer notes continued confusion surrounding legal liability in the case of disputed assessments.
Digital Government
Lawmakers: Did DHS Surveil Portland Protesters’ Phones?
Lawmakers want to know if federal agencies intercepted messages or collected cellphone data—including through commercial sources—during Portland protests.
Cybersecurity
Foreign Hacker Sentenced in $1M Scam Targeting Federal Employees and Contractors
The criminal ring used phishing emails and fake websites to get almost $1 million worth of printer toner to sell on black markets.
Cybersecurity
How to shift CMMC for the future
While the goal of Cybersecurity Maturity Model Certification is to establish a unified standard for cybersecurity practices across the DOD, it does not directly address specific control expectations or risks associated with organization-specific threat actors.
Cybersecurity
CMMC clears key regulatory hurdle
The White House approved an interim rule to mandate defense contractors prove they adhere to existing cybersecurity standards from the National Institute of Standards and Technology.
Cybersecurity