Cyber Threats Will Keep Coming if Public and Private Sectors Don't Collaborate, Says DHS Cyber Exec

Finchen/Shutterstock.com
Securing the cyber ecosystem against national threats requires a partnership between government and industry players, according to a DHS cyber official.
Public-private partnerships are the key to robust national cybersecurity, according to Peter Fonash, chief technology officer for the Department of Homeland Security's Cybersecurity and Communications Office. Still, they're unlikely to happen until both sectors can communicate better.
Cyber breaches have been getting worse over the years, Fonash said during a recent conference in Washington, D.C. He referenced two key statistics from a recent Verizon Data Breach Investigation Report that shows two particular trend-lines between 2004 and 2013: one for the percent of time that compromising a system took a day or less, and another, much lower, for the percent of time that the discovery of breaches took a day or less.
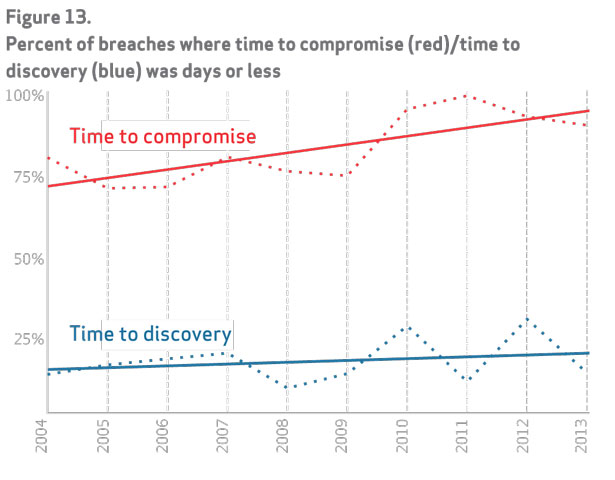
“Unfortunately, the slope of the [bad guys'] curve is greater than the slope of the good guys,” he said. “How we do business today is not working. The problem was bad in [2004], and it’s gotten worse in 2013. And I would suspect the trend is not getting better.”
DHS works with the National Security Agency, the FBI, and other organizations on cybersecurity, focusing primarily on protecting dot-gov systems, Fonash said. Their programs include the intrusion prevention system Einstein, whose sensors are meant to monitor Internet traffic, and “Enhanced Cybersecurity Services," which aims to help businesses strengthen their cybersecurity protection.
During his remarks, Fonash said securing the cyber ecosystem against national threats requires a partnership between the government and industry players.
”We need to be able to share information much more rapidly than we currently do," he said.
One way to do so, he said, is through an automated system. But first, industry and government must agree on a set of standards for sharing cyber threat information, Fonash stressed. Currently, as CERT receives information, "we have to translate it from one format to another format," he said.
Authentication is another important factor in such a system, Fonash said, adding, “If I share information with you, I have to know who I’m sharing it with.”
Without systems like this, Fonash said, the chart depicting rapid-fire cyber breaches “is going to continue on.”
(Image via Finchen/ Shutterstock.com)
NEXT STORY: Debating the Sino-Russian cyber pact





