Hackers Can Listen In on Your Skype Calls

Twin Design/Shutterstock.com
A security researcher found a way to “piggyback” on video chats, and it’s very hard to detect.
Mark Zuckerberg covers up his laptop’s camera with a little piece of tape. After he posted a photo of himself at a desk this summer celebrating Instagram’s growing popularity, online commenters seized on the little gray strip above his laptop screen. “You Should Consider It, Too,” read a headline on The New York Times, calling Zuckerberg’s move a “basic and cheap security safeguard.”
The tape trick keeps hackers from secretly recording you through your laptop’s webcam. It essentially functions as an off button for the camera, physically preventing it from recording until you take off the tape to make a video call.
But new research suggests hackers can eavesdrop on those video calls, too, when you think you and the person you’re talking to are the only ones on the line.
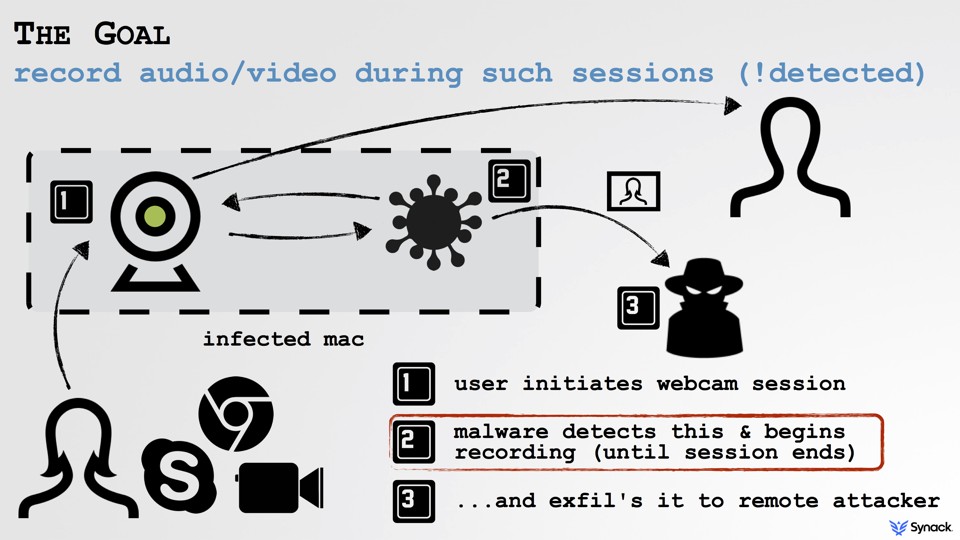
Patrick Wardle, the director of research at a cybersecurity company called Synack, showed how hackers might do this at a cybersecurity conference called Virus Bulletin on Thursday. (Wardle used to work for NASA and the National Security Agency.) He calls the technique “piggybacking,” because it relies on a computer’s user to do most of the legwork: Instead of secretly turning on the webcam without the user’s permission, piggybacking malware simply waits until the webcam is active, and then records everything it sees.
The piggybacking process is simple: A malware program quietly running in the background of a computer checks periodically to see if someone has activated the camera. When the camera is turned on, the malware starts recording, too, alongside Skype or FaceTime, and stops recording when the session ends. Finally, the malware sends the recording to the attacker.
The genius of this kind of an attack, Wardle says, is that it’s virtually undetectable. When the camera on a Mac laptop starts recording, it also turns on a green indicator light. Disabling that light is almost impossible without physically taking apart a laptop, so if it unexpectedly turns on, it’s pretty clear that something’s up.
But when you initiate a video chat, you’re already expecting that green LED to illuminate—so the malware can piggyback on the recording without raising suspicion. It then shuts itself off when the video call is over to allow the light to turn off, too.
Eavesdropping on a video call is probably more useful than recording at random intervals, because that’s when people share sensitive or important information.
“If you infected my Mac and recorded me all the time, you’d see me sitting at my desk, picking my nose, petting my dog, and occasionally swearing at my computer,” Wardle said. “However, when I jump on a Google Hangout to discuss a new [software vulnerability] with a vendor—that’s when things get interesting.”
As a side project, Wardle creates free Mac utilities that protect computers from the security problems he discovers. To make video piggybacking harder, he created a program called Oversight, which displays a notification every time a program starts recording via the webcam. If the notification says Skype wants access, you can click “Allow.” If a fishy-sounding program is trying to access the camera, or if a second notification pops up while you’re already on a video call, you can hit “Deny” to shut it down.
Wardle emphasizes the piggybacking technique doesn’t take advantage of any unknown vulnerability or manipulate Apple’s operating systems. It uses only legitimate features built into macOS—just in a clever and potentially dangerous way. Does piggybacking malware exist in the wild? It could, Wardle says, but he hasn’t seen any examples other than the program he himself built to test his theory.
He did alert Apple to his experimentation, and recommended Macs send users a notification whenever a program wants to use a laptop’s webcam or a microphone. But apart from that, there’s not really anything to be done, short of rebuilding significant portions of macOS.
“I doubt Apple will do anything about this,” Wardle said. “And honestly, I’m not sure they should.” (Apple declined to comment.)
In the meantime, keep covering up those webcams—even the FBI director does it—and consider downloading a utility like Oversight that can tell you whether or not you’re alone on your next video call.
NEXT STORY: New federal CISO is in it for the long haul






