Coming soon to a military theater near you: The Age of Surprise
U.S. Air Force
Air Force grad students, video producers air trailer-like preview of conflict in 2035.
Air Force officers have posted to YouTube an apparent trailer for a Hollywood movie about cyberwarfare in 2035 that’s actually a game plan for the Pentagon. The Meta-Strategy for the Age of Surprise is the brainchild of Air University graduate students, an instructor with a knack for video blogging, and a part-time professional production team paid less than $3,000.
The two-minute audiovisual uses quick-moving photographs and imagery synchronized with jarring orchestral music to deliver a narrative.
“Very short videos with a lot of images and good sound are more appealing than long videos with a guy like me yapping,” said Lt. Col. Ed “Hertz” Vaughan, Age of Surprise executive producer and the creator of a 2010 video series called Dispatches from Antarctica , which chronicles military research on the continent through a video diary. “I learned through that experience and I could see which videos got a lot of hits.”
The student video has been watched more than 19,400 times since quietly posting on Sept. 9. It will be formally released to top Defense Department officials in October.
The short movie takes viewers along a pictorial timeline of air innovations beginning with Leonardo da Vinci’s hang glider through the first hot air balloon launch, Wright Brothers airplane flight, satellite liftoff, and other aviation milestones to developments affecting all military domains, such as Facebook, denial-of-service computer attacks, biotechnology and nanotechnology.
The new data paradigms affect military operations on land, at sea, in the air and space because, as the video declares, “Information travels everywhere. Anyone can access anything.”
The storyline depicts a new mind-set needed to confront whatever unfamiliar threats surface decades from now. The film is based on annual papers by the Blue Horizons graduate student program published between 2009 and 2012. The goal of the flick is not to recruit scholars or to obtain funding from the powers that be, but rather to stimulate debate.
The premise is future combat will demand that warfighters reimagine airpower with the arrival of each new technology from dogfighting to data fighting, cloud services and 3-D printing -- an automated process that can mass produce industrial parts such as airplane wings typically requiring hundreds of workers to build.
“Most of the buzzwords at the end came from the new class,” which arrived in July, Vaughan said. “With ‘data fighting,’ you can imagine two warriors duking it out in cyberspace.”
The video does not advocate for specific weapons. “This is not intended to lead to or influence any immediate decisions on funding or strategy right now,” Vaughan said. “We did intend for the senior leaders at the Pentagon to see the video. We also want to guide them to our research.
Some YouTube visitors who commented on the video’s home page objected to the pace of progress portrayed.
“When will people stop falling for this accelerationist con job? The video itself illustrates technological stagnation in aeronautics because we've relinquished supersonic air travel and continue to use subsonic airliners originally designed in the 1960s and 1970s. The SR-71 Blackbird, designed by guys with slide rules in the 1960s, still looks and performs like something out of science fiction,” one Internet user wrote.
Other observers suggested the momentum of advancement, which is represented by the timeline contorting into a growth curve, moves too quickly: “I gotta say, my favorite part is when the [atomic] bomb hits the exponential curve and we see that we are approaching the knee of the curve. However, I think it escalates too quickly around 2000. We are not that vertical yet.”
The Air Force official moderating the online discussion explained the chart is not meant to symbolize the mathematical growth function of air, space and cyber.
The trends illustrated relate to overall national security risks, according to Vaughan. “If we can prepare for some of this, it actually prevents us from needing to go to war,” he said.
The 16 individuals in the course, “most of whom are combat veterans, many of whom are combat veterans many times over,” were assigned to look 20 to 30 years into the future, he said. Vaughan also founded Wingman Project , an outreach program that aims to end suicide among airmen and their family members.
For the Blue Horizons effort, Vaughan’s job was to translate students’ words into content understandable to the movie production team and vice versa.
During a five-week period, the producers, none of whom had military backgrounds, found noncopyrighted images of aircraft produced during the same years shown in the timeline -- such as rockets flown during the War of 1812.
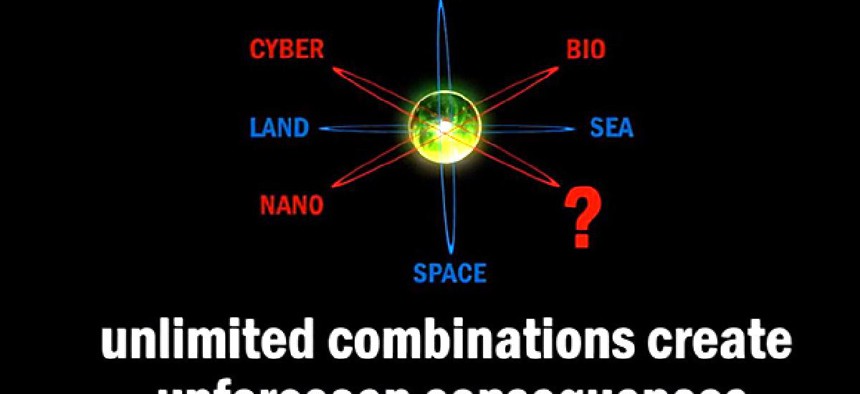
One of the most important visuals, Vaughan said, is an atom-like model of the four warfighting domains, which next sprouts three more domains -- for cyber, biotech and nano. “And then you see a question mark. That’s the domain that we just don’t know right now,” he said.
NEXT STORY: Rising Star: Benjamin Black






