3 Lessons Agencies Need to Learn from WannaCry
Egorov Artem/Shutterstock.com
First, the outbreak isn't over.
Federal government systems escaped the global outbreak of the WannaCry ransomware, but agencies can glean lessons to fend off whatever comes next, experts told lawmakers Thursday.
“Federal systems were fortunately spared from WannaCry, but we want to make sure they’re spared in a more sophisticated attack,” said Rep. Darin LaHood, R-Ill., chairman of the House Science, Space and Technology Research and Technology Subcommittee.
» Get the best federal technology news and ideas delivered right to your inbox. Sign up here.
Lawmakers seemed optimistic that when agencies adopt the National Institute of Standards and Technology’s Cybersecurity Framework—as mandated by a May executive order—it will improve their security footing. Here are other takeaways:
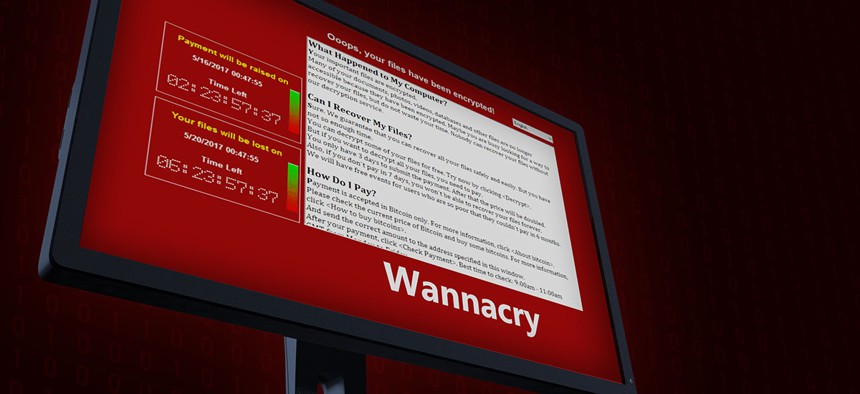
The WannaCry outbreak isn’t over.
WannaCry consisted of two parts: the ransomware payload that encrypts files and demands payment and the self-replicating worm. A Kryptos Logic employee deftly found a “kill switch” for the ransomware after the outbreak started May 12. The worm, however, continues infecting systems without its creators intervening.
The largest attack happened June 8 and 9, attempting to infect a U.S. hospital about 275,000 times, Kryptos Logic CEO Salim Neino said.
Patches must be applied and kept up to date, he said.
Agencies should pay more attention to response and recovery.
Agencies focus more on prevention than what to do when an attack happens, Charles Romine, director of NIST’s Information Technology Laboratory, said. He pointed to the Federal Information Security Management Act and the Cybersecurity Framework as good foundations, though NIST also issued guidance specifically for what to do after an incident occurs.
“The Boy and Girls Scouts are right: Their motto is to be prepared,” Romine said.
Neino suggests running “fire drills” for staff but also as part of the larger community. He suggested a scale for cyberattacks—like the Richter scale for earthquakes—so organizations can easily understand the severity.
“Response and recovery planning is an essential part of cyber risk management,” Symantec CEO Hugh Thompson said. “We will not always have luck on our side.”
Someone needs to make sure agencies meet cybersecurity requirements, but who is up for debate.
In March, the committee passed the NIST Cybersecurity Framework, Assessment and Auditing Act, which includes a section that would expand NIST’s role from offering guidance to auditing agency compliance.
NIST’s current role is scientific, focused on collecting information from the private sector, academia and other government agencies to distill best practices it then shares.
“Assigning NIST duties to lead auditing or compliance activities changes those relationships and not in a good way,” former federal Chief Information Security Officer Greg Touhill wrote in his testimony. “I have had numerous senior colleagues confess to me it likely will inhibit or stifle the free exchange of information from public and private entities to NIST.”
Agency inspectors general, he said, already have the culture and expertise to audit.






