Federal Cybersecurity by the Numbers: The Biggest Spenders and the Biggest Threats

Tammy54/Shutterstock.com
The annual scorecard tracking agencies’ compliance with the Federal Information Security Management Act shows some agencies are backsliding.
Over the couple years, cyberincidents reported by federal agencies have nearly doubled -- from about 41,000 in 2011 to more than 77,000 last year.
Partly that’s because agencies are getting smarter about detecting threats, such as suspicious network activity or malware able to slip past traditional antivirus tools.
But the annual scorecard tracking agencies’ compliance with the Federal Information Security Management Act shows some agencies are, in fact, backsliding when it comes to robust security measures.
The following charts show how agencies have plugged long-festering critical vulnerabilities, which agencies are ponying up the most cash for IT security and some of the common threats faced across agencies.
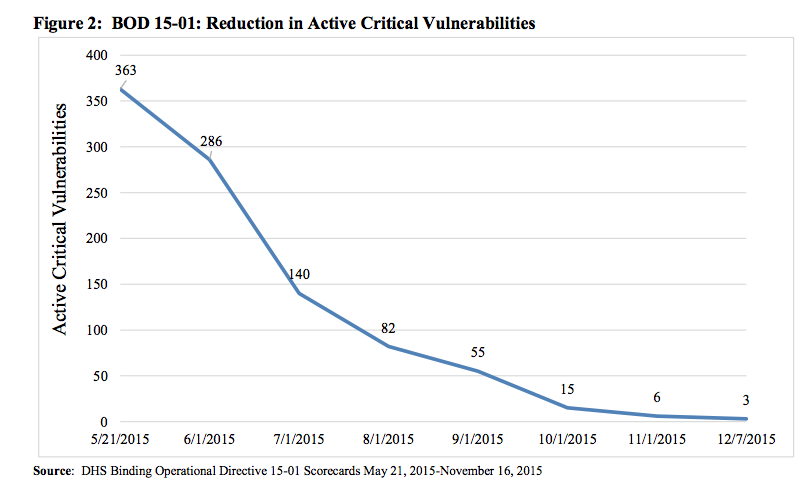
First, the good news. The chart above shows the progress agencies, under orders from the Homeland Security Department, made patching the number of active critical vulnerabilities. Congress empowered DHS, through 2014 legislation, to issue “binding operational directives” for fixing urgent problems. DHS first used the authority last spring in the wake of the massive hack of background check records at the Office of Personnel Management.
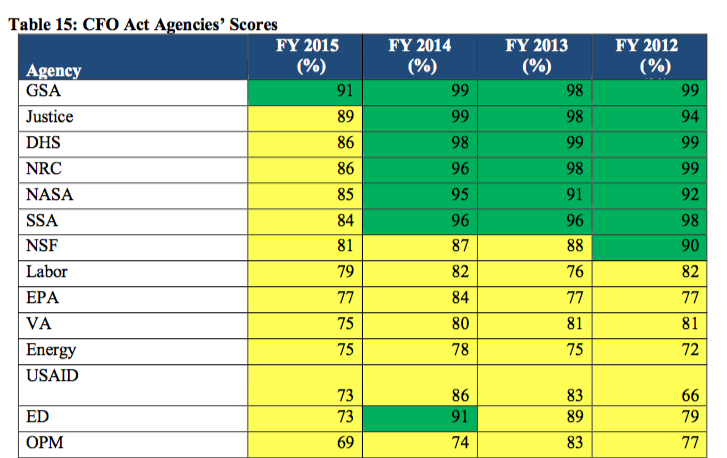
However, fewer agencies last year received passing grades from their inspectors general, who are responsible for examining agencies’ information security programs. The chart above shows just one agency -- the General Services Administration -- scored higher than 90 percent on the assessment. That’s down from five agencies in the previous year’s report. The average score of 68 percent is an 8 percent decrease from the last report.
The IG grades are based on reviews of agencies security processes, including continuous monitoring of cyberthreats, identity and access management, incident response and other areas.
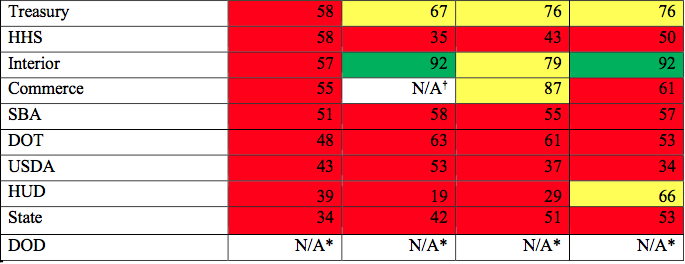
In addition to fewer high-scoring agencies, more agencies flunked this year’s assessment. The departments of Treasury, Interior and Commerce, who all earned passing grades the previous year, dipped into the red this year. Interior completely nosedived from a score of 92 percent in the last report to just 57 percent.
Why did governmentwide scores lower? Because of new more stringent scoring requirements, which showed that while most agencies have continuous monitoring programs in place, they’re not very effective, according to the report.
No surprise the Defense Department is far and away the biggest spender on information security -- dropping $9.1 billion last year on security tools and services. The only other agency to crack eight figures was DHS. It’s not shown on the chart above, but the most frugal agency when it comes to infosec spending was -- of all agencies -- OPM. Even with the massive hack last year, the agency spent just $7 million on cybersecurity.
This spending does not encompass all IT spending by an agency. Instead, it covers spending on things like intrusion prevention tools, cyber threat analysis, employee security testing, identity management tools and incident response services.
As we already noted, federal agencies reported more than 77,000 “cyberincidents” to the U.S. Computer Emergency Readiness Team last year. However, that term encompasses a wide variety of activity. Not all of it is all that nefarious and some incidents don't really have much to do with computers. For example, agencies across government reported 12,217 “noncyber” incidents last year, which don’t have anything to do with sophisticated hackers and could simply describe misfiled paperwork.
Still, other incidents are more serious. The chart above shows the number of successful denial-of-service attacks reported by agencies last year. Target No. 1: DHS. Still, such attacks on federal websites are relatively rare as far as reported cyberincidents go.
The chart above shows the number of malware attacks reported by agencies. Last year, NASA reported more than 1,500 successful downloads of malware that had not been immediately quarantined or wiped out by regular antivirus protection. In contrast, OPM (not shown in the chart) reported just four successful malware attacks.
Finally, the DHS-run EINSTEIN intrusion-detection and prevention tool picked up more than 2,900 cases of suspicious network activity. The reported cases are compiled from incident reports automatically generated by EINSTEIN.





